An indictment and arrests followed the seizure of a notorious cybercrime gang’s website after a rare international operation, with two of the criminals being Russian nationals.
The FBI and Britain’s National Crime Agency led an effort to arrest and indict members of the LockBit ransomware gang after law enforcement took control of their website.
The United States unsealed an indictment on Tuesday charging two Russian nationals with deploying LockBit ransomware against companies and groups worldwide, the Department of Justice (DOJ) announced.
Obtained in New Jersey, the unsealed indictment charges Artur Sungatov and Ivan Kondratyev, also known as Bassterlord, with using LockBit ransomware to target victims in manufacturing, logistics, insurance, and other companies in five states and Puerto Rico, as well as in semiconductor and other industries around the world.
Additional criminal charges against Kondratyev were unsealed on Tuesday related to his use of ransomware in 2020 against a victim in California, the DOJ said.

In addition to the U.S. indictments, police in Poland and Ukraine also made two arrests, Europol Deputy Executive Director Operations Jean-Philippe Lecouffe told reporters.
“An unprecedented amount of data gathered from this investigation is now in the hands of law enforcement,” he said.
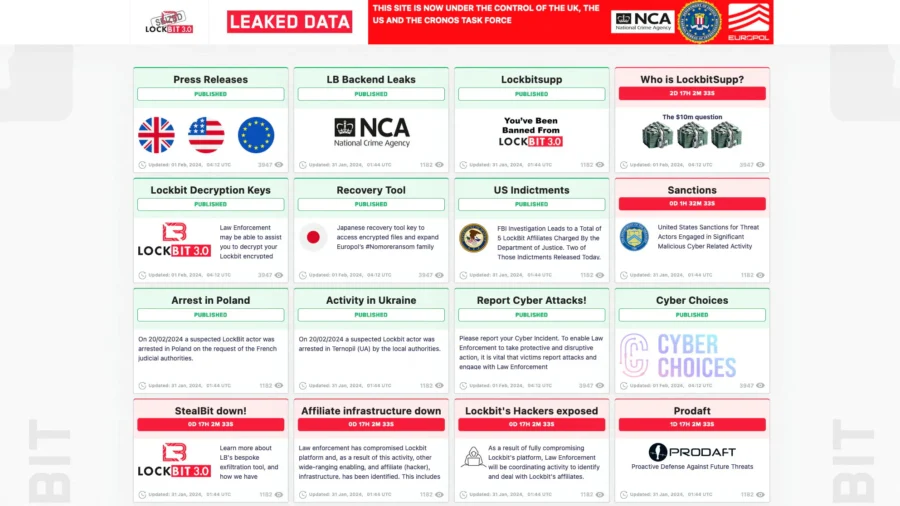
The indictment was made public as the NCA, DOJ, FBI, and Europol gathered in London to announce the disruption of the gang.
LockBit has targeted over 2,000 victims worldwide, received more than $120 million in ransom payments, and demanded hundreds of millions of dollars, the DOJ said.
Officials in the United States have described LockBit as the world’s top ransomware threat, which has targeted financial services, food, schools, transportation, and government departments.
Britain’s NCA, the FBI, and international law enforcement agencies from Australia, Japan, Canada, and across Europe cooperated in the operation.
“We have taken control of their infrastructure, seized their source code, and obtained keys that will help victims decrypt their systems,” Graeme Biggar, director general of the National Crime Agency, told journalists.
The law enforcement operation was dubbed “Operation Cronos.” “Together, we have arrested, indicted, or sanctioned some of the perpetrators and we have gained unprecedented and comprehensive access to LockBit’s systems.”
“As of today, LockBit is effectively redundant,” he added. “LockBit has been locked out.”
LockBit and its affiliates have hacked some of the world’s largest organizations in recent months. The gang makes money by stealing sensitive data and threatening to leak it if victims fail to pay a ransom. Its affiliates are like-minded criminal groups that Lockbit recruits to wage attacks using its digital extortion tools.
Ransomware is malicious software that encrypts data. LockBit makes money by coercing its targets into paying ransom to decrypt or unlock that data with a digital key.
Before it was taken down, LockBit’s website displayed an ever-growing gallery of victim organizations that was updated nearly daily. Next to their names were digital clocks that showed the number of days left to the deadline given to each organization to provide ransom payment.
In November last year, LockBit published internal data from Boeing, one of the world’s largest defense and space contractors. In early 2023, Britain’s Royal Mail faced severe disruption after an attack by the group.
On Tuesday, the LockBit leak website had been transformed by the NCA, FBI, and Europol into a leak site about the criminal gang itself, onto which international police agencies published internal data from inside the group and countdown clocks threatening to reveal upcoming sanctions and the identity of LockBit’s ringleader, “LockBitSupp.”
A member of LockBit posted messages on an encrypted messaging app saying it had backup servers not affected by the law enforcement action.
LockBit is dominated by Russian speakers and does not attack former Soviet nations. Officials suggested that LockBit could have hundreds of members, but there’s no evidence that a nation-state like Russia is behind the gang, Mr. Biggar said.
“These are criminals,” he said, although the lack of a Russian crackdown indicates that Moscow tolerates the gang’s activity.
The operation is “probably the most significant ransomware disruption to date,” Analyst Brett Callow of the cybersecurity firm Emsisoft said. And while it will likely spell the end of the brand, such groups routinely rebrand and re-emerge under new names. Over the long term, Mr. Callow said, this operation alone will not diminish the volume of ransomware attacks.
Last week, LockBit claimed responsibility for the cyberattack on Fulton County, saying it had gained access to the state citizens’ personal data and threatened to leak the data if the ransom was not paid.
Fulton County Chairman Robb Pitts confirmed to local media outlets that the outage was related to a cyberattack and had impacted operations at the Fulton County Superior Court clerk’s office and other services.
LockBit was discovered in 2020 when its eponymous malicious software was found on Russian-language cybercrime forums, leading some security analysts to believe the gang is based in Russia.
Britain’s National Cyber Security Centre has previously warned that ransomware remains one of the biggest cyber threats facing the U.K. and urges people and organizations not to pay ransoms if they are targeted.
Reuters, Aldgra Fredly, and The Associated Press contributed to this report.